Summary
Netskope Threat Labs is tracking a phishing campaign that mimics a FedEx package delivery as bait to steal credit card data. This type of social engineering attack is commonly found in phishing pages, emails, and other scams, where a false sense of urgency is created to urge the victim into doing an action that eventually leads to personal data theft.
This specific phishing campaign is noteworthy because it abuses two cloud services throughout the attack: TrustedForm, a digital certificate service provided by ActiveProspectis, is abused to track victims and collect information about them, and the PAAY 3DS, a cloud-based platform that authenticates payment transactions, is abused to validate the credit card details collected from the victims.
Cybersecurity awareness training, specifically educating users to be wary of fake shipment notifications, is an effective defense against these types of phishing attacks. Netskope customers also receive protection from the threats discussed in this blog through the Next Generation Secure Web Gateway (SWG).
First Stage – Deception
The attack starts when the victim receives an email or a text message that uses a common social engineering technique, creating a false sense of urgency to get the victim’s attention. The specific approach here, using a fake shipping notification, is also a common technique used by scammers.
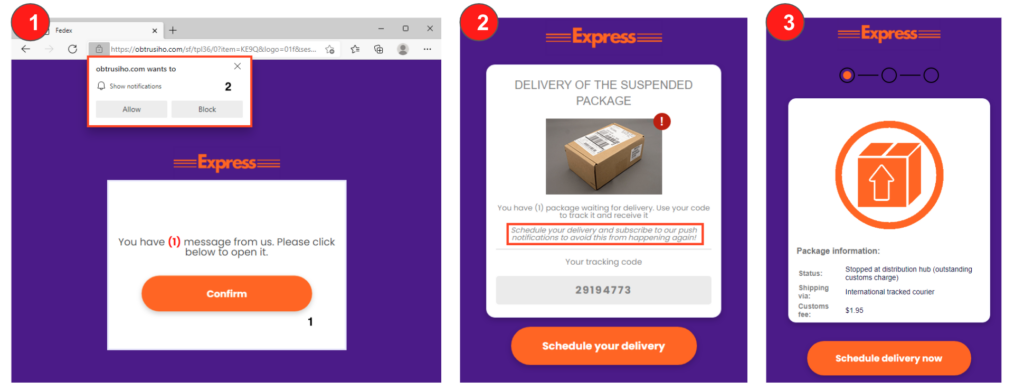
Step 1 – Once the victim reaches the page via phishing email or SMS text, they are instructed to click “Confirm” to view a message from “Express.” This webpage has “FedEx” in the title and uses the same company colors to deceive the user. The user is also asked to permit push notifications in the browser, which allows the attacker to push malicious ads, as we will demonstrate later in this analysis.
Step 2 – The victim is informed that delivery of a package has been suspended, and that they need to schedule delivery and should enable push notifications to avoid future issues.
Step 3 – Then, the victim is informed that they need to pay a $1.95 customs fee. The customs fee is just an excuse to collect the victim’s personal and credit card data in the next stage of the attack.
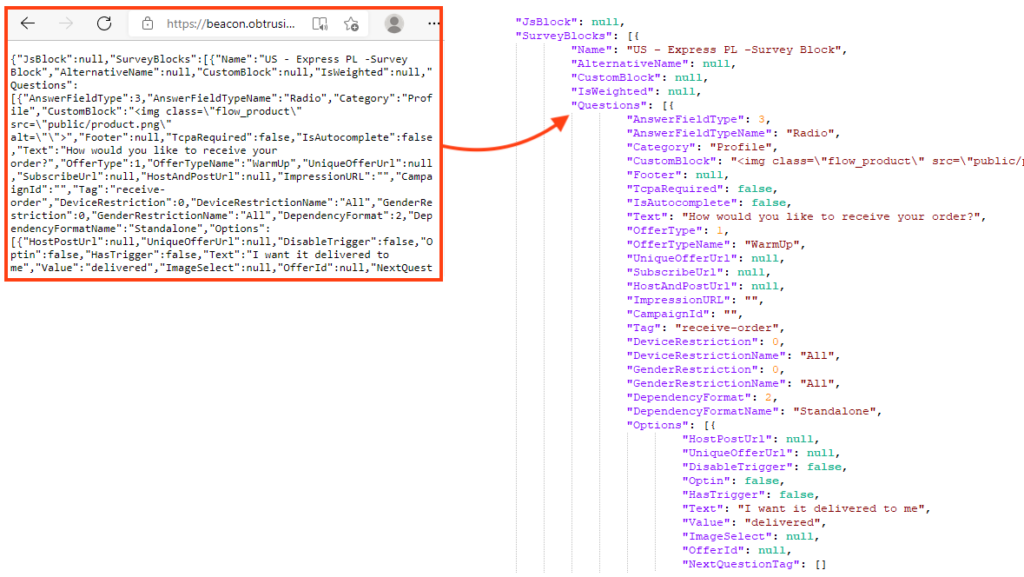
Behind the scenes, once the first page is loaded, the page sends a request to receive a customizable JSON that is used throughout the attack. The JSON includes the questions, form fields, and second-stage URLs, which will be all used in the next steps.
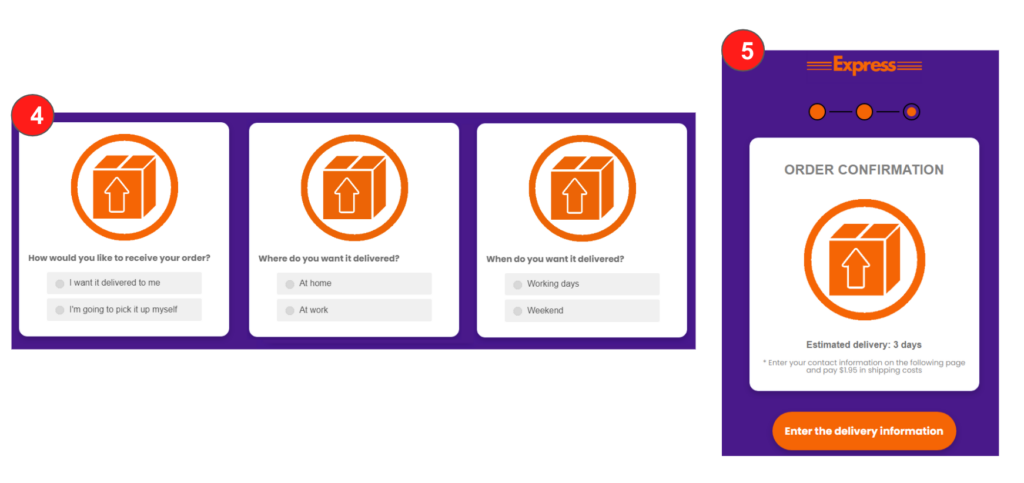
Step 4 – The attacker continues to deceive the victim, in an attempt to add more credibility to the phish, by asking a series of questions to the victim, such as how, where, and when the victim would like to receive the package.
Step 5 – The deception continues by giving the victim a delivery estimate.
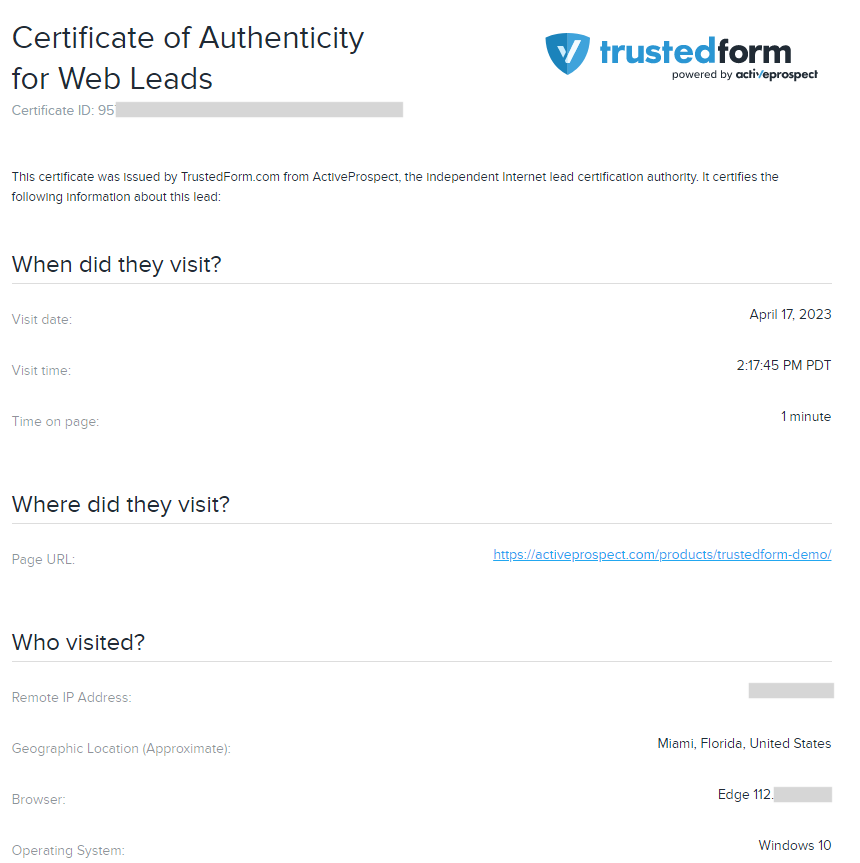
As soon as the victim interacts with the questions on step 4, the phishing starts sending requests to the TrustedForm API. TrustedForm is a digital certificate service provided by ActiveProspect, which provides marketing automation and compliance platforms. This service can be used to generate a digital certificate that includes information about a lead, such as geolocation, IP address, browser type, operating system, the time spent on the page, and even a web session replay. We believe that the attacker is creating a TrustedForm certificate to collect more information about victims.

Below is the type of information that would be available in a TrustedForm certificate, as demonstrated in their demo webpage.
And finally, the phishing page redirects the victim to the next stage, using a URL parsed from the JSON we demonstrated earlier. This page returns a second URL, which is used to redirect the user to a third URL. This is done to add resilience, as the attacker can update the URLs with little effort if the last stage is taken down.
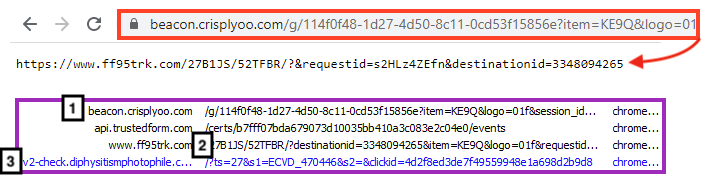
Second Stage – Stealing Credit Card Data
Once the attacker convinces the victim about the allegedly suspended package, they try to steal the victim’s credit card number on a different page.
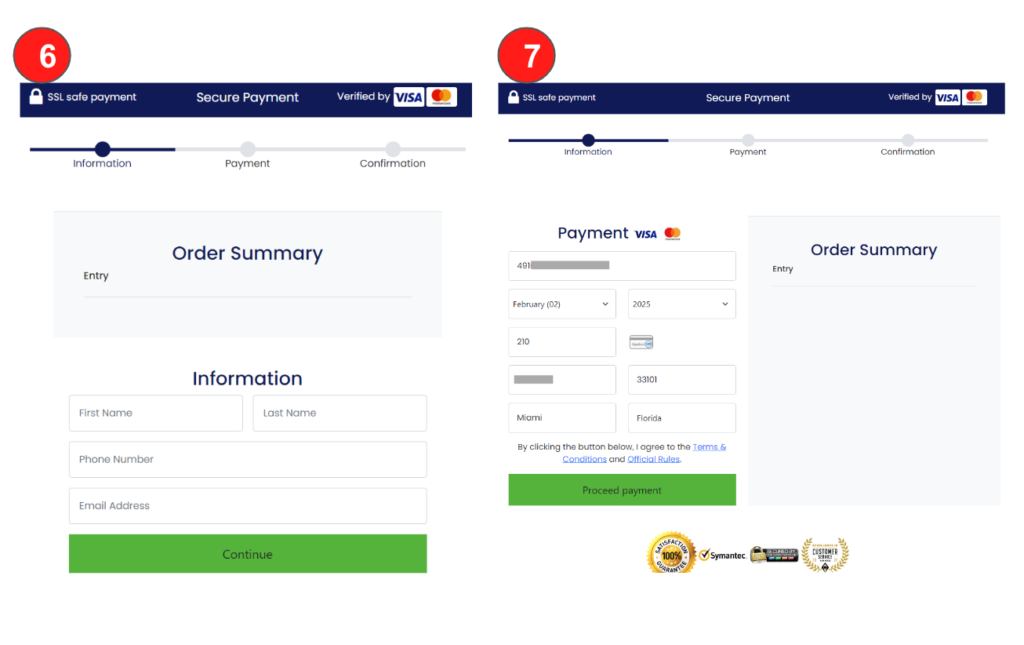
Step 6 – This page asks for the victim’s personal information, such as the full name, phone number, and email address.
Step 7 – Then, the page asks for credit card details and uses PAAY to assess whether the credit card is valid. This is done by using their 3DS (3-D Secure) system, which is a protocol designed to add more security and prevent fraud in online purchases.
Once the credit card data is entered in the page, it starts sending requests to the 3DS API, which performs a temporary purchase in the credit card number. If the credit card is invalid, the phishing does not move forward.
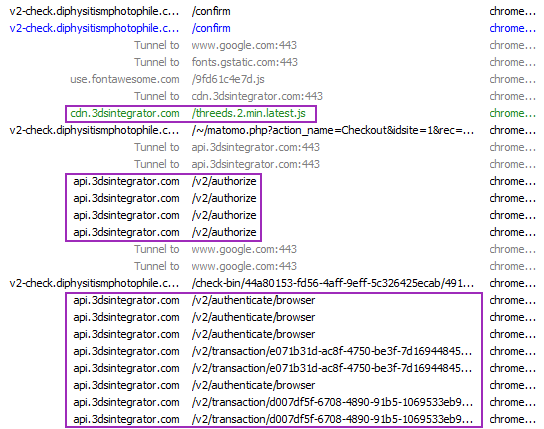
Spreading Adware
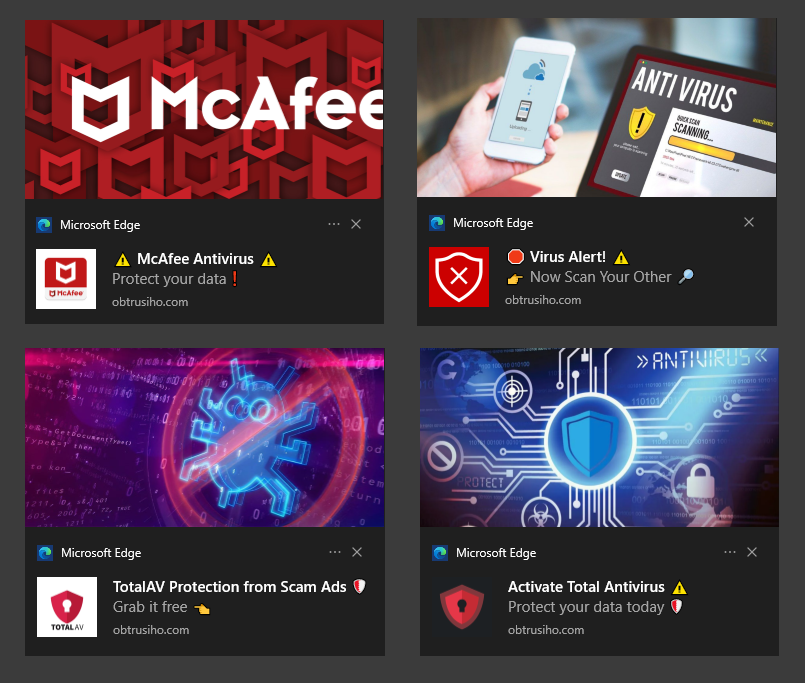
As demonstrated earlier, the main page asks for permission to show notifications in the browser. Unsurprisingly, if the victim allows notifications, they are bombarded with ads from the “virtualpushplatform[.]com” domain, including ads for fake antivirus software, fake coupons, and free iPads.
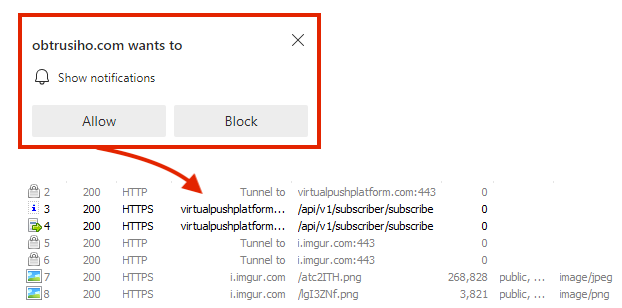
These ads lead to webpages that eventually ask for personal information or try to download malware. So, even in case the phishing attack fails at any stage, if the victim allows notifications, they will still be targeted with additional scams.
Conclusions
By abusing cloud services, attackers are able to create more elaborate phishing pages that are also more resilient to detection. This phishing campaign is not only trying to steal data from victims, but also abuses browser notifications to bombard victims with additional scams even if this one is unsuccessful. Netskope uses ML-based inline, out-of-band phishing detection engines, and threat intelligence systems to block such phishing attempts.
Recommendations
Phishing pages from the campaign described in the post are easily recognizable by the URL, as the attacker has made little effort to disguise the URL using typosquatting or other techniques. We strongly recommend users to never enter their data on pages that promise something, such as the delivery of a supposedly suspended package. If you are indeed expecting a package, make sure to access the website of the logistics company directly.
Netskope Threat Labs also recommends that organizations review their security policies to ensure that they are adequately protected against these and similar phishing pages and scams:
- Inspect all HTTP and HTTPs traffic, including all web and cloud traffic, to prevent users from visiting malicious websites. Netskope customers can configure their Netskope NG-SWG with a URL filtering policy to block known phishing and scam sites, and a threat protection policy to inspect all web content to identify unknown phishing and scam sites using a combination of signatures, threat intelligence, and machine learning.
- Use Remote Browser Isolation (RBI) technology to provide additional protection when there is a need to visit websites that fall in categories that can present higher risk, like Newly Observed and Newly Registered Domains.
IOCs
Below are the IOCs related to the web pages analyzed in this blog post.
URLs
hxxps://biriata[.]com/ff0787bfecd727e800/7_783335_2683580/2357_2741426_4412557_61/505175864_163-116-145-33
hxxps://entfernza[.]com/sf/tpl36/0?item=KE9Q&logo=01f&session_id=f8e48861-bc10-40e7-bd05-e152979e4ee7&sub1=ECVD_470446&sub5=0c1fd02a-51fd-474b-8954-1b700f38e0b9
hxxps://giggingge[.]com/sf/tpl36/0?item=KE9Q&logo=01f&session_id=b3beae86-91be-4ef4-8d2e-6f0a07b6ce7d&sub1=ECVD_470446&sub5=ee2c5954-324d-43da-8830-00445bd703e8#!/hst
hxxps://obtrusiho[.]com/sf/tpl36/?item=KE9Q&logo=01f&session_id=eb178549-389d-4fd5-aa8c-adc714552d94&sub1=ECVD_470446&sub5=6a64a541-0f1f-4cc0-b655-3048f97e148e#!/hst
hxxps://crisplyoo[.]com/sf/tpl36/0?item=KE9Q&logo=01f&session_id=742f8239-2017-4771-a6dc-ee09dc744bad&sub1=ECVD_470446&sub5=e4fdd22d-4394-49cf-8742-403d38df3a8c#!/hst
hxxps://vod-7.zoonosisdewlap[.]com/
hxxps://v2-check.caducitymatroclinic[.]com/
hxxps://v2-check.turriferouscouloir[.]com/
hxxps://v2-check.diphysitismphotophile[.]com/
Domains
biriata[.]com
entfernza[.]com
giggingge[.]com
obtrusiho[.]com
crisplyoo[.]com
vod-7.zoonosisdewlap[.]com
v2-check.caducitymatroclinic[.]com
v2-check.turriferouscouloir[.]com
v2-check.diphysitismphotophile[.]com




 Voltar
Voltar 





















 Leia o Blog
Leia o Blog